Leads4Pass CCSA 156-215.81 exam materials shared online

Leads4Pass CCSA 156-215.81 exam materials are the latest exam materials, including 400 latest exam questions and answers, covering more than 91.4% of actual exam questions.
Download the latest CCSA 156-215.81 exam materials with PDF and VCE: https://www.leads4pass.com/156-215-81.html, judging from the June pass rate, the success rate of 99.5% can ensure that you pass easily take an exam.
Leads4Pass Latest CCSA 156-215.81 Exam Materials:
| Total number of materials | Share online | Material provider |
| 400 Q&A | 15Q&A | Leads4Pass.com |
Question 1:
What command from the CLI would be used to view current licensing?
A. license view
B. fw ctl tab -t license -s
C. show license -s
D. cplic print
Correct Answer: D
The command cplic print displays the installed licenses and their expiration dates on the CLI. References: Check Point CLI Reference Card
Question 2:
Fill in the blank: Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or__________.
A. On all satellite gateway to satellite gateway tunnels
B. On specific tunnels for specific gateways
C. On specific tunnels in the community
D. On specific satellite gateway to central gateway tunnels
Correct Answer: C
Permanent VPN tunnels can be set on all tunnels in the community, on all tunnels for specific gateways, or on specific tunnels in the community. This option allows the administrator to select which tunnels should be permanent and which
should be established on demand. The other options are not valid, as they do not match the available choices in the VPN community settings.
References: [VPN Administration Guide], [Check Point R81.10]
Question 3:
Fill in the blank: The position of an implied rule is manipulated in the __________________ window.
A. NAT
B. Firewall
C. Global Properties
D. Object Explorer
Correct Answer: C
The position of an implied rule is manipulated in the Global Properties window. Implied rules are predefined rules that are not displayed in the rule base. They allow or block traffic for essential services such as communication with Check Point servers, logging, and VPN traffic. The position of an implied rule can be changed in the Global Properties > Firewall > Implied Rules section. References: How to view Implied Rules in R80.x / R81.x SmartConsole, Implied Rules
Question 4:
Which command shows the installed licenses in Expert mode?
A. print click
B. show licenses
C. folic print
D. click print
Correct Answer: D
The command that shows the installed licenses in Expert mode is click print. This command displays information about the licenses that are installed on the local machine or a remote machine. The other commands are not valid for showing licenses in Expert mode.
Question 5:
Which two of these Check Point Protocols are used by?
A. ELA and CPD
B. FWD and LEA
C. FWD and CPLOG
D. ELA and CPLOG
Correct Answer: B
The two Check Point Protocols that are used are FWD and LEA. FWD is the Firewall Daemon that handles communication between different Check Point components, such as Security Management Server, Security Gateway, SmartConsole, etc. LEA is the Log Export API that allows external applications to retrieve logs from the Security Gateway or Security Management Server. Therefore, the correct answer is B. FWD and LEA. References: Border Gateway Protocol – Check Point Software, Check Point IPS Datasheet, List of valid protocols for services? – Check Point CheckMates
Question 6:
What is the purpose of the Clean-up Rule?
A. To log all traffic that is not explicitly allowed or denied in the Rule Base
B. To clean up policies found inconsistent with the compliance blade reports
C. To remove all rules that could have a conflict with other rules in the database
D. To eliminate duplicate log entries in the Security Gateway
Correct Answer: A
The purpose of the Clean-up Rule is to log all traffic that is not explicitly allowed or denied in the Rule Base. The Clean-up Rule is the last rule in the rule base and is used to drop and log explicitly unmatched traffic. To improve the release performance, noise traffic that is logged in the Clean-up rule should be included in the Noise rule so it is matched and dropped higher up in the rule. The other options are not valid purposes of the Clean-up Rule. References: Using Intune device cleanup rules, Security policy fundamentals, Support, Support Requests, Training, Documentation, and Knowledge base for Check Point products and services
Question 7:
What is the default shell for the command line interface?
A. Clish
B. Admin
C. Normal
D. Expert
Correct Answer: A
Clish is the default shell for the command line interface. It is a user-friendly shell that provides a menu-based and a command-line mode. Admin, Normal, and Expert are not valid shell names.
Question 8:
DLP and Geo Policy are examples of what type of Policy?
A. Inspection Policies
B. Shared Policies
C. Unified Policies
D. Standard Policies
Correct Answer: B
DLP and Geo Policy are examples of Shared Policies. Shared Policies are policies that can be shared with other policy packages to save time and effort when managing multiple gateways with similar security requirements. Shared Policies
can be applied to Access Control, Threat Prevention, and HTTPS Inspection layers. Other types of policies include Inspection Policies, Unified Policies, and Standard Policies. References:
[Check Point R81 Security Management Administration Guide], [Check Point R81 SmartConsole R81 Resolved Issues]
Question 9:
View the rule below. What does the pen symbol in the left column mean?
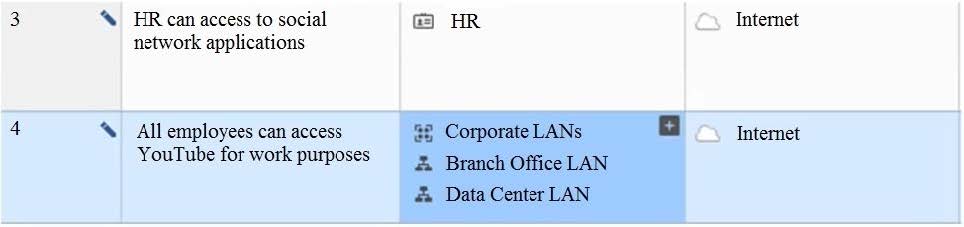
A. Those rules have been published in the current session.
B. Rules have been edited by the logged-in administrator, but the policy has not been published yet.
C. Another user has currently locked the editing rules.
D. The configuration lock is present. Click the pen symbol to gain the lock.
Correct Answer: B
The pen symbol in the left column means that the rules have been edited by the logged-in administrator, but the policy has not been published yet. It indicates that the changes are not yet effective and can be discarded. References: Policy Editor, Publishing Changes
Question 10:
The Online Activation method is available for Check Point manufactured appliances. How does the administrator use the Online Activation method?
A. The SmartLicensing GUI tool must be launched from the SmartConsole for the Online Activation tool to start automatically.
B. No action is required if the firewall has internet access and a DNS server to resolve domain names.
C. Using the Gaia First Time Configuration Wizard, the appliance connects to the Check Point User Center and downloads all necessary licenses and contracts.
D. The cpinfo command must be run on the firewall with the switch -online-license- activation.
Correct Answer: C
The Online Activation method is available for Check Point manufactured appliances. The administrator uses the Online Activation method by using the Gaia First Time Configuration Wizard, the appliance connects to the Check Point User Center and downloads all necessary licenses and contracts. This method requires internet access and a valid User Center account. References: [Check Point Licensing and Contract Operations User Guide], [Check Point R81 Gaia Installation and Upgrade Guide]
Question 11:
Choose what BEST describes users on Gaia Platform.
A. There are two default users and neither can be deleted.
B. There are two default users and one cannot be deleted.
C. There is one default user that can be deleted.
D. There is one default user that cannot be deleted.
Correct Answer: A
There are two default users on Gaia Platform and neither can be deleted. The two default users are admin and monitor. The admin user has full access to the Gaia configuration and management tools, such as CLI and WebUI. The monitor user has read-only access to the Gaia configuration and management tools, and can only view the system status and settings. These two users cannot be deleted, but their passwords can be changed. References: [Gaia Administration Guide], [Gaia Overview]
Question 12:
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
A. Full
B. Custom
C. Complete
D. Light
Correct Answer: A
The type of Endpoint Identity Agent that includes packet tagging and computer authentication is Full. The Full Identity Agent is a client-side software that provides full identity awareness features, such as user authentication, computer authentication, packet tagging, identity caching, and identity sharing. The other types of Endpoint Identity Agents are Custom, Complete, and Light, which have different features and capabilities.
Question 13:
Which of the following is NOT a tracking option? (Select three)
A. Partial log
B. Log
C. Network log
D. Full log
Correct Answer: ACD
The options that are not tracking options are Partial log, Network log, and Full log. Tracking options are settings that determine how the Security Gateway handles traffic that matches a rule in the security policy. The valid tracking options are Log, Detailed Log, Extended Log, Alert, Mail, SNMP trap, User Defined Alert, and None. The other options are incorrect. A log is a tracking option that records basic information about the traffic, such as source, destination, service, action, etc. Detailed Log is a tracking option that records additional information about the traffic, such as NAT details, data amount, etc. Extended Log is a tracking option that records even more information about the traffic, such as matched IPS protections, application details, etc. References: [Logging and Monitoring Administration Guide R80 – Check Point Software]
Question 14:
If the Active Security Management Server fails or if it becomes necessary to change the Active to Standby, the following steps must be taken to prevent data loss. Providing the Active Security Management Server is responsible, which of these steps should NOT be performed:
A. Rename the hostname of the Standby member to match exactly the hostname of the Active member.
B. Change the Standby Security Management Server to Active.
C. Change the Active Security Management Server to Standby.
D. Manually synchronize the Active and Standby Security Management Servers.
Correct Answer: A
The correct answer is A because renaming the hostname of the Standby member to match exactly the hostname of the Active member is not a recommended step to prevent data loss. The hostname of the Standby member should be different from the hostname of the Active member. The other steps are necessary to ensure a smooth failover and synchronization between the Active and Standby Security Management Servers. References: Check Point R81.20 Administration Guide, 156-315.81 Checkpoint Exam Info and Free Practice Test
Question 15:
Which application is used for the central management and deployment of licenses and packages?
A. SmartProvisioning
B. SmartLicense
C. SmartUpdate
D. Deployment Agent
Correct Answer: C
SmartUpdate is the application that is used for the central management and deployment of licenses and packages. SmartUpdate allows administrators to manage licenses, software updates, and hotfixes for multiple Security Gateways and cluster members from one central location. SmartProvisioning is an application that enables centralized management of network devices. SmartLicense is a feature that simplifies license management by using a cloud-based portal. Deployment Agent is a component that enables automatic deployment of software packages.
| More related | Important hint |
| checkpoint exam materials | Become a Leads4Pass member to access the complete materials |
Summary: All certifications are for better employment. On indeed.com you can see the companies you want to work for in the future. Leads4pass CCSA certification materials: https://www.leads4pass.com/156-215-81.html helps you successfully pass the exam, obtain certification, and implement the next step.